Firefox’s latest Enhanced Tracking Protection gave users the option to block cookies and storage access from third-party trackers.
In October 2018, Mozilla.org announced the release of Firefox’s Enhanced Tracking Protection (ETP). ETP gave users the option to block cookies and storage access from third-party trackers. The intent was to give users more control over data they share and to block the most common forms of cross-site tracking. To help with added protection, using the best vpn for firefox or a VPN that suits when working online, may be able to squash site tracking even further and help users feel safer when they are on the browser.
On September 3, 2019, Firefox v69.0 was released, enabling ETP for both new and existing users. This change makes blocking third-party tracking cookies and cryptominers the default setting. It also blocks known trackers in all Private windows:
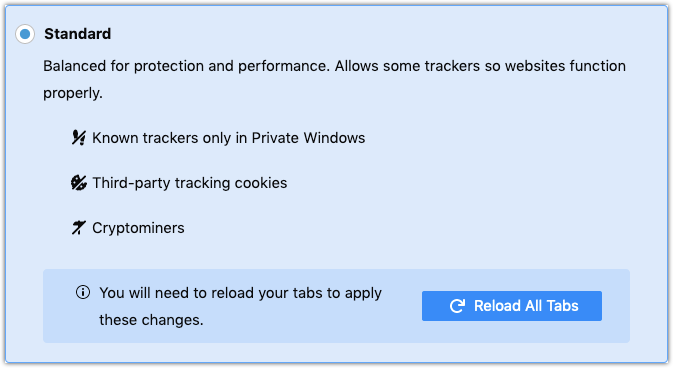
In addition to the Standard settings shown above, a Strict option exists that blocks fingerprinters and known trackers in all windows. For complete v69.0 release details, see the official Mozilla release notes.
Impact to website analytics
While the idea behind these changes is not new, the forced enablement of them is, and the impact on analytics data is real. At a minimum, anonymous visitor identification is hampered, making it less likely that a cookie can be reliably set for consistent identification across sessions. To the extreme, entire tag delivery networks or tag management systems can be blocked as they are identified as known tracking domains, resulting in a complete loss of analytics and marketing data (and possibly user experience issues).
How you can maintain data integrity as browser privacy evolves
This most recent change in the browser privacy landscape is specific to Firefox, but Safari and Chrome have also made recent privacy-related changes, as well. And, going forward, we fully expect continued evolution across all browsers.
As you evaluate your website’s analytics and marketing beacon implementations, consider the following as potential steps toward continued data integrity in an ever-changing world of browser security and privacy:
- Move away from third-party cookies and cookies set using document.cookie
- Where possible, self-host or leverage CNAME solutions to serve third-party scripts – including TMS libraries – from first-party domains
- Implement server-side beaconing solutions and integrations where client-side implementations are not required
The Evolytics team recognizes that each situation is unique, and what works for one website or app may not work for another. If you have questions about your situation, please let us know.
